There’s a growing need for transparency in the world of cryptocurrency as vulnerabilities in hardware wallets can expose users to significant risks. Responsible security research aims to uncover these weaknesses while promoting accountable disclosure practices to minimize potential harm. Investigating these vulnerabilities not only protects individual users but also enhances the overall security of the blockchain ecosystem. By fostering collaboration between researchers and manufacturers, the industry can achieve a safer environment for digital asset management.
Key Takeaways:
- Responsible security research emphasizes the importance of disclosing vulnerabilities to manufacturers before public announcements.
- Hardware wallet vulnerabilities can lead to significant financial loss and undermine user trust in security technologies.
- Collaboration between researchers and companies can enhance product security and facilitate timely patches.
Understanding Hardware Wallets
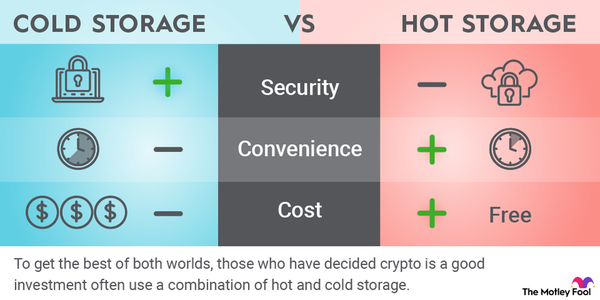
For individuals investing in cryptocurrencies, the security of their assets is paramount. Hardware wallets are a type of device specifically designed to store private keys offline, providing a safer environment against online threats. By keeping the keys isolated from internet connections, hardware wallets significantly reduce the risk of hacking, phishing, and malware attacks, ensuring users maintain control over their cryptocurrency.
Definition and Functionality
Before entering into the specifics, it’s necessary to define what a hardware wallet is: a physical device that securely stores cryptocurrency private keys. Unlike software wallets that may be vulnerable to online threats, hardware wallets utilize secure elements and often require physical interaction to perform transactions, enhancing their security. Transactions can be signed within the wallet itself, keeping the private keys hidden from potentially compromised computers.
Popular Hardware Wallets in Use
Among the various hardware wallets available today, some of the most prominent include the Ledger Nano S, Ledger Nano X, and Trezor Model T. These devices are heralded for their robust security features, user-friendly interfaces, and support for a vast range of cryptocurrencies. They ensure users have reliable options for securely managing their crypto assets, combining convenience and safety.
Definition: These popular hardware wallets have gained traction due to their strong security measures, such as two-factor authentication and PIN protection. Users can benefit from enhanced safety while transacting in the volatile cryptocurrency market. By using such hardware wallets, individuals can safeguard their investments from cyberattacks and other threats, ensuring peace of mind in managing their digital assets.
Security Vulnerabilities in Hardware Wallets
Clearly, hardware wallets are not impervious to threats and can exhibit security vulnerabilities that may compromise the safety of users’ digital assets. While these devices are designed with a robust security architecture, weaknesses can arise due to design flaws, manufacturing defects, or user errors. Detecting and mitigating these vulnerabilities is necessary for maintaining the confidence of users in such critical technological solutions.
Common Types of Vulnerabilities
Between various vulnerabilities observed in hardware wallets, some of the most common include:
| Type of Vulnerability | Description |
| Firmware Flaws | Errors in software that can be exploited. |
| Physical Attacks | Unauthorized manipulation or access to the hardware. |
| Malicious Updates | Infected firmware installations that compromise security. |
| Side-Channel Attacks | Extracting information via unintended leaks during operation. |
Perceiving the importance of addressing these vulnerabilities is necessary for the ongoing enhancement of hardware wallet security.
Case Studies of Vulnerability Exploits
After examining various case studies, it becomes evident that hardware wallets have succumbed to notable exploits. Some significant instances of this include:
- 2017 LedgerSome of the links on this page are affiliate links. If you purchase a cold wallet through these links, we may earn a commission at no extra cost to you. Nano S: A vulnerability allowed that an attacker could access the private keys through an insecure Bluetooth connection, with thousands of wallets compromised.
- TrezorSome of the links on this page are affiliate links. If you purchase a cold wallet through these links, we may earn a commission at no extra cost to you. One: In 2018, a side-channel attack was demonstrated, enabling attackers to extract sensitive data from the wallet, affecting hundreds of users.
- KeepKey: An exploit in 2019 was reported that utilized malicious code to intercept PIN codes during entry, endangering thousands of accounts.
Types of such vulnerabilities highlight the most important impacts on user security and present positive takeaways for manufacturers to strengthen their protocols against these threats. Awareness of these exploits provides valuable insights for strengthening security measures and fostering user education concerning the risks involved in using hardware wallets.
Responsible Disclosure Practices
Keep in mind that responsible disclosure practices are important for maintaining the integrity of hardware wallets and their user base. By ensuring that vulnerabilities are reported and addressed in a timely manner, researchers play a pivotal role in safeguarding sensitive information and financial assets. This collaborative approach fosters trust between developers and the security community, ultimately enhancing the security posture of the entire ecosystem.
Importance of Responsible Disclosure
Above all, responsible disclosure serves to mitigate the risks associated with vulnerabilities before they can be exploited by malicious actors. By reporting vulnerabilities through designated channels, researchers help manufacturers develop and implement fixes, protecting users from potential threats. This proactive communication reduces the likelihood of public exposure that could lead to widespread damage, ensuring that any fixes are distributed swiftly and effectively.
Steps for Responsible Vulnerability Reporting
Practices for responsible vulnerability reporting typically involve several key steps that researchers should follow. Initially, it’s important to gather all relevant information about the vulnerability, including detailed descriptions, potential impacts, and replication steps. Next, researchers should contact the hardware wallet manufacturer through appropriate channels, adhering to their guidelines for submission. After notifying the vendor, a timeline for public disclosure should be established, allowing the manufacturer time to address the issue without unnecessary panic among users.
Vulnerability reporting should focus on timely and clear communication to the affected company to facilitate a swift resolution. Researchers should provide comprehensive documentation detailing the findings, including potential impacts and exploit scenarios, allowing the vendor to understand the severity and urgency. Additionally, adhering to an agreed timeline for public disclosure not only demonstrates professionalism but also enables the vendor to implement fixes effectively, ensuring that users are protected while still promoting transparency in the security community.
The Role of Security Researchers
Unlike many other sectors, the field of hardware wallet security relies heavily on the expertise of security researchers to identify and mitigate risks. These professionals play a significant role in uncovering vulnerabilities that may otherwise go unnoticed, contributing to the overall security of the cryptocurrency ecosystem. Through their rigorous testing and analysis, researchers help establish a more secure environment for users seeking to protect their assets.
Responsibilities and Ethics
Researchers must approach their work with a strong sense of responsibility and ethics. This involves not only identifying vulnerabilities but also reporting them in a way that minimizes potential harm to users. Failing to disclose findings responsibly can lead to exploitation of identified weaknesses, resulting in significant losses for individuals and companies alike.
Ensuring a balance between the needs of the public and the interests of the developers is vital. Researchers are expected to adhere to responsible disclosure practices, providing developers with the opportunity to address vulnerabilities before publicizing findings. Adhering to these principles fosters trust and collaboration between researchers and developers.
Collaborating with Hardware Wallet Developers
Collaborating with hardware wallet developers is crucial for enhancing security measures and fostering innovation. By engaging in open dialogue, researchers can share findings and insights that allow developers to implement necessary improvements more effectively. This partnership helps create products that not only meet current security needs but also evolve with emerging threats.
In fact, such collaboration leads to more robust security frameworks for hardware wallets, allowing developers to patch vulnerabilities efficiently. The exchange of information often results in enhanced user awareness regarding security best practices. By working together, both researchers and developers can significantly reduce the risk of exploitation, ultimately promoting a safer cryptocurrency environment for users.
Mitigating Risks and Improving Security
Your approach to hardware wallet security should incorporate a blend of best practices and proactive measures. Regularly updating wallet firmware is imperative to protect against newly discovered vulnerabilities. Users should also utilize strong, unique passwords and enable biometric authentication features where available to add an additional layer of security.
Recommendations for Wallet Users
On a personal level, ensure that your hardware wallet is purchased directly from the manufacturer or authorized retailers to avoid tampering risks. Additionally, always set up wallets in a secure environment and never share recovery phrases with anyone. Engage in community forums and stay informed about potential vulnerabilities, which can provide timely insights into safeguarding your assets.
Suggestions for Manufacturers
One of the primary responsibilities manufacturers have is implementing robust security protocols throughout the development and delivery phases of hardware wallets. This includes conducting regular security audits, collaborating with independent security researchers for vulnerability testing, and establishing clear communication channels for reporting and addressing security issues.
Manufacturers must prioritize the inclusion of hardware-enforced security features and ensure that their products are backed by transparent security practices. Emphasizing continuous improvement through user feedback and adhering to evolving security standards will enhance credibility and trust in their devices. By fostering a culture of responsible security research, manufacturers can better protect users and their digital assets from emerging threats.
Final Words
Presently, the landscape of hardware wallet security continues to evolve, demanding ongoing vigilance and proactive measures from developers and researchers alike. The responsible disclosure of vulnerabilities plays a pivotal role in enhancing the overall security posture of these devices. By fostering a collaborative relationship between security researchers and manufacturers, the industry can better address potential threats before they escalate.
Moreover, transparency in the disclosure process not only helps build trust among users but also promotes a culture of accountability within the sector. As consumers increasingly rely on hardware wallets for safeguarding their assets, it is imperative that both manufacturers and researchers remain committed to upholding high standards of security, ultimately benefiting the entire cryptocurrency ecosystem.
FAQ
Q: What is a hardware wallet vulnerability disclosure?
A: A hardware wallet vulnerability disclosure is the process of responsibly reporting security flaws or weaknesses found in hardware wallets, which are designed to securely store cryptocurrency private keys. This ensures that the issue can be addressed before it is exploited by malicious actors.
Q: How should a security researcher report a vulnerability in a hardware wallet?
A: A security researcher should follow best practices for responsible disclosure by directly contacting the hardware wallet manufacturer or vendor, providing detailed information about the vulnerability, and allowing them sufficient time to address the issue before making the information public.
Q: What are the benefits of responsible vulnerability disclosure for hardware wallets?
A: Responsible vulnerability disclosure helps enhance the overall security of hardware wallets, builds trust between manufacturers and users, and encourages a collaborative approach to improving security standards across the cryptocurrency ecosystem.







