Security is paramount in the world of cryptocurrency, especially when it comes to cold wallets. Cold wallet stress testing serves as an necessary safeguard, evaluating how these wallets perform under extreme conditions and potential attack scenarios. By identifying vulnerabilities during simulated pressure situations, users can fortify their assets against serious threats that could jeopardize their investments. This proactive approach not only boosts confidence in wallet security but also fosters trust in handling digital currencies effectively.
Key Takeaways:
- Cold wallets can experience vulnerabilities under high-pressure scenarios, highlighting the need for regular stress testing.
- Evaluating security measures during potential attack simulations helps identify weaknesses and improve overall resilience.
- Comprehensive testing protocols must include various threat vectors to ensure robust cold wallet protection.
Understanding Cold Wallets
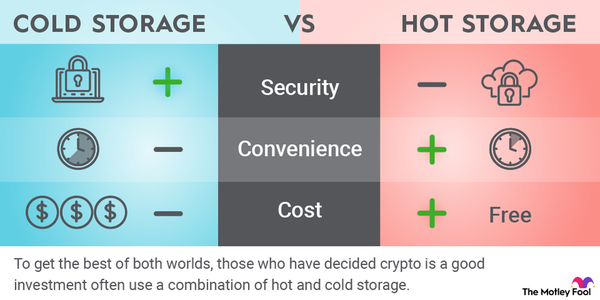
Your cold wallet acts as a secure storage solution for cryptocurrencies, isolating them from online threats. The primary purpose of these wallets is to protect digital assets from hacks, malware, and other cyber risks while providing users with a way to store their cryptocurrency offline.
Definition and Purpose
Between the various options for storing cryptocurrency, cold wallets stand out for their ability to keep assets away from internet vulnerabilities. By removing the keys necessary for transactions from the online realm, cold wallets offer enhanced security compared to their hot wallet counterparts.
Types of Cold Wallets
Between the various types of cold wallets, users can choose from hardware wallets, paper wallets, and air-gapped devices. Each option provides different levels of convenience and security, and understanding their features can help users select the appropriate method for holding their assets.
| Type | Description |
| Hardware Wallet | Physical device securing private keys offline. |
| Paper Wallet | Printed QR codes or keys for storing assets. |
| Air-Gapped Wallet | Computers not connected to the internet for transactions. |
| Metal Wallet | Engraved metal strips for durability against damage. |
| Cold Card Wallet | Specialized devices focused on Bitcoin security. |
Hence, exploring the strengths and weaknesses of each cold wallet type is vital for effective asset protection. Popular choices include hardware wallets, which combine security and usability, and paper wallets, known for their offline safety.
- Hardware Wallets
- Paper Wallets
- Air-Gapped Devices
- Metal Wallets
- Cold Card Wallets
Recognizing the importance of choosing the right type of cold wallet can greatly influence the security of your cryptocurrency holdings.
Importance of Stress Testing
Now, the significance of stress testing cold wallets cannot be overstated. In a world where cyber threats are constantly evolving, ensuring that cryptocurrency storage solutions are resilient under various conditions is necessary. Stress testing provides insights into vulnerabilities that might not be apparent under normal operations, revealing potential weaknesses before they can be exploited. By subjecting cold wallets to simulated attacks or adverse conditions, users can ascertain their effectiveness in safeguarding assets and bolster overall security protocols.
Assessing Security Risks
With the increasing sophistication of cyber threats, assessing security risks through stress testing is vital. By identifying the limitations of cold wallets, users can develop better security strategies tailored to their specific environmental factors. Stress testing can uncover flaws in hardware, software, or user practices, enabling a proactive approach to security rather than a reactive one. Additionally, understanding these risks helps in choosing the right cold wallet solutions and implementing stronger protective measures.
Real-World Scenarios
Against the backdrop of evolving hacker techniques, stress testing cold wallets against real-world scenarios helps in understanding potential attack vectors. By simulating conditions such as physical theft, power outages, or network breaches, organizations can evaluate their readiness and adaptability in facing actual threats. This preparation is necessary as it provides insight into how the wallet performs under distress, ensuring that users are not caught off guard during critical times.
Importance of stress testing lies in its ability to prepare users for various attack scenarios that could potentially lead to asset loss. By conducting tests simulating physical theft, power failures, or unauthorized access, users gain valuable insights that inform their security strategies. This kind of realistic evaluation is instrumental in identifying weaknesses and ensuring that cold wallets can withstand the most dangerous threats, ultimately maintaining the integrity of users’ investments.
Methodologies for Stress Testing
For an effective evaluation of cold wallet security, various methodologies can be employed to simulate real-world scenarios that might put the wallet under significant pressure. These methodologies aim to identify vulnerabilities and assess the overall integrity of the wallet when subjected to high-risk environments. Through rigorous testing, vulnerabilities can be uncovered before malicious actors exploit them in actual situations.
Simulating Attacks
Around cybersecurity, simulating attacks can be an enlightening experience for revealing potential security flaws in cold wallets. Techniques such as DDoS simulations, where multiple simulated requests overwhelm the wallet’s interfaces, can provide insight into how the wallet withstands aggressive online threats. Additionally, phishing simulations can help evaluate the wallet’s response to social engineering attempts that might compromise private keys.
Evaluating System Response
Methodologies employed during the evaluation of system responses should focus on the wallet’s ability to maintain operations under duress. The tests can include monitoring transaction processing times, power consumption, and overall performance when simulating multiple attack vectors. An effective cold wallet should exhibit resilience and sustain operational integrity even when subjected to intense pressure.
Simulating stress scenarios helps in understanding both the technical limitations and overall effectiveness of the wallet’s security measures. Each test can lead to the identification of weaknesses, allowing for timely adjustments to be made and enhancing the wallet’s defenses. The objective is to ensure that any response to attack scenarios can safeguard the wallet assets, reinforcing the credibility of its security architecture.
Common Vulnerabilities in Cold Wallets
After assessing the security architecture of cold wallets, it’s vital to recognize their vulnerabilities. While cold wallets are inherently more secure than their hot counterparts, they are not immune to risks that can compromise the integrity of the stored assets. Effective cold wallet security requires vigilance, as attackers continually refine their methods to exploit weaknesses.
Physical Security Risks
At the core of physical security risks is the tangible nature of cold wallets. Devices like USB drives or hardware wallets are susceptible to theft or physical tampering. If an attacker gains access to the wallet itself, they can extract sensitive information or access private keys, leading to asset loss. Proper storage in a safe location is necessary to mitigate these risks.
Software Flaws
Any software flaws present in the wallet’s firmware or accompanying applications can pose significant threats. Vulnerabilities such as outdated versions, lack of security patches, or poor cryptographic implementations can open doors for attackers, allowing unauthorized access to private keys or compromising transaction integrity. Ensuring software is up to date and reviewing security practices is vital for maintaining safety.
But even with current software, complexities can arise. Vulnerabilities may not only stem from the wallet software itself but also from third-party tools or services used in conjunction with the wallet. Attackers often exploit these connections, making it imperative for users to thoroughly vet all software before integration. Moreover, rigorous testing and validation are vital to ensure underlying software operatesas intended, without introducing vulnerabilities that could jeopardize asset security.
Best Practices for Cold Wallet Security
All cold wallet users should prioritize security by implementing several best practices to safeguard their assets against unauthorized access. These measures include using strong, unique passwords, employing hardware wallets rather than paper wallets, and ensuring that wallets are stored in secured locations. Additionally, conducting thorough research on any cold wallet solution is important to assess its security features and customer reviews.
Enhancing Physical Protection
For optimal security, cold wallet owners must enhance physical protection methods. This can be achieved by storing wallets in a safe or a secure location, away from elements that could compromise their integrity. Using fireproof and waterproof containers can also provide an extra layer of security, thus minimizing damage from unforeseen circumstances.
Regular Software Updates
Security experts recommend consistent software updates to protect cold wallets against vulnerabilities. Outdated software can expose wallets to exploitation from malicious actors looking for gaps in security. By routinely checking for and applying updates, users can enhance their wallet’s functionality and protect against emerging threats.
And utilizing automated update notifications can aid in maintaining the wallet’s security without the need for constant manual checks. A proactive approach towards software maintenance is vital, as neglecting these updates leaves wallets susceptible to attacks that could result in significant financial loss. Ensuring that all software used in conjunction with cold wallets is up-to-date reinforces a robust security posture.
Case Studies in Cold Wallet Stress Testing
Many organizations have conducted cold wallet stress tests to evaluate security measures under various simulated attack scenarios. These studies highlight the importance of robust security protocols and the different outcomes based on their methodologies. Key findings from various case studies include:
- Case Study 1: A financial institution tested its cold storage against DDoS attacks, resulting in a 75% downtime but no loss of assets.
- Case Study 2: A cryptocurrency exchange simulated physical theft scenarios and found that implementing biometric security reduced breach attempts by 90%.
- Case Study 3: A private investment firm evaluated recovery processes, revealing that 60% of users were unaware of proper recovery methods, highlighting the need for training.
- Case Study 4: An NGO tested their cold wallets against social engineering tactics, with 30% of employees inadvertently disclosing sensitive information despite training.
Successful Stress Tests
By analyzing the outcomes from successful stress tests, it becomes evident that certain strategies greatly enhance the resilience of cold wallets. For example, institutions that implemented multi-layered security measures saw a significant reduction in vulnerability. In one case involving a large bank, integrating advanced encryption methods resulted in no successful breaches during the stress testing phase, underscoring the importance of robust cryptography in safeguarding assets.
Furthermore, organizations that prioritized employee training on security protocols demonstrated a marked improvement in their ability to thwart social engineering attacks. Regular drills and workshops led to a 50% increase in employees identifying phishing attempts accurately, showcasing that human factors play a vital role in overall security posture.
Lessons Learned
One of the most significant takeaways from these case studies is that existing protocols require constant adaptation to emerging threats. Organizations discovered that routine assessments are imperative in identifying weaknesses before attackers can exploit them. For instance, the NGO that faced social engineering issues implemented monthly training sessions, resulting in fewer successful attempts over time.
Further analysis reveals that not all organizations placed enough emphasis on employee training or incident response plans, leading to unnecessary losses during tests. A holistic approach that includes not only technological upgrades but also a strong focus on human capability is vital for achieving long-term security and resilience in cold wallet systems.
To wrap up
Conclusively, Cold Wallet Stress Testing serves as an imperative method for assessing the security measures of cryptocurrency storage solutions under adverse conditions. By simulating intense pressure scenarios, organizations can identify vulnerabilities and reinforce defenses, ultimately enhancing the overall integrity of their cold wallet systems. This proactive approach helps ensure that assets remain protected against both external threats and internal failures.
Moreover, continuous evaluation through stress testing fosters confidence among users and investors by demonstrating a commitment to security excellence. As the landscape of digital assets evolves, prioritizing thorough and adaptive testing methodologies will be vital in maintaining robust security standards, thereby safeguarding the future of cryptocurrency financial transactions.
FAQ
Q: What is cold wallet stress testing?
A: Cold wallet stress testing involves simulating various attack scenarios and operational stresses on a cold wallet to evaluate its ability to withstand potential security threats without compromising the integrity and safety of stored assets.
Q: Why is stress testing important for cold wallets?
A: Stress testing identifies vulnerabilities and weaknesses in a cold wallet’s security system that could be exploited under pressure. This process ensures that the wallet can maintain its functionality and secure assets even during extreme conditions or attacks.
Q: What types of threats are considered during cold wallet stress testing?
A: Threats include physical attacks (e.g., theft, tampering), cyberattacks (e.g., hacking attempts, malware), and operational stresses (e.g., power failures, system overloads). Evaluating these scenarios helps in fortifying the wallet’s resilience against diverse security challenges.